Cloud Privileged Access Management (PAM) software is designed to manage and secure access to critical systems and data within cloud environments. It focuses on controlling and monitoring the activities of users who have elevated permissions or administrative rights. Here’s a breakdown of what it typically involves:

- Access Control: PAM software restricts access to sensitive systems and resources based on roles and permissions. It ensures that only authorized users can access specific cloud resources.
- Session Management: It tracks and records the activities of users with privileged access during their sessions. This helps in monitoring and auditing what actions are being performed.
- Password Management: PAM systems often include features for securely storing and rotating passwords for privileged accounts, reducing the risk of unauthorized access.
- Least Privilege Enforcement: PAM solutions enforce the principle of least privilege by granting users only the permissions they need for their tasks and nothing more. This minimizes potential damage in case of a compromised account.
- Monitoring and Auditing: It provides detailed logs and reports on privileged account activity, helping organizations to detect and respond to suspicious behavior or compliance issues.
- Risk Management: By controlling and monitoring privileged access, PAM helps mitigate risks associated with data breaches, insider threats, and misconfigured systems.
Cloud PAM is crucial for maintaining security and compliance in environments where multiple users may have elevated access, ensuring that sensitive information and critical systems are protected.
Saviynt
Saviynt’s cloud PAM software solution is delivered via an agentless, zero-touch architecture so you can deploy privileged access management in days.
- Secure Every Identity With Zero Trust
- Certify Least Privilege Access With Built-in Governance
- Collaborate Securely With External Users
- Secure Multi-Cloud Workloads and Accelerate Cloud Adoption
- Execute at Scale With True PAM & Identity Convergence
Britive
Britive, the first true dynamic cloud privileged access management with patented dynamic, JIT ephemeral access allows for fine-grained controls to establish security guardrails without slowing teams down.
- Dynamic, Ephemeral Access Across the Cloud
- DevOps Friendly, Security Approved
- Eliminate Friction, Increase Productivity
Oneidentity
One Identity privileged access management (PAM) solutions allow you to monitor privileged users and improve security while maintaining compliance requirements.
- One Identity Cloud PAM Essentials
- Privileged session management
- Privileged password vault
- Privileged threat analytics
- Least privileged access
- UNIX identity consolidation
- Privileged access governance
Axiom.security
Axiom’s access management platform streamlines permission requests, approvals, and management for cloud, SaaS, and database environments.
- Identity-Based vs. Network-Based Security
- Modern Cloud Access Tools
- Granularity and Dynamic Needs
- Scalability and Automation
- Rich Integrations and Great User Experience
Strongdm
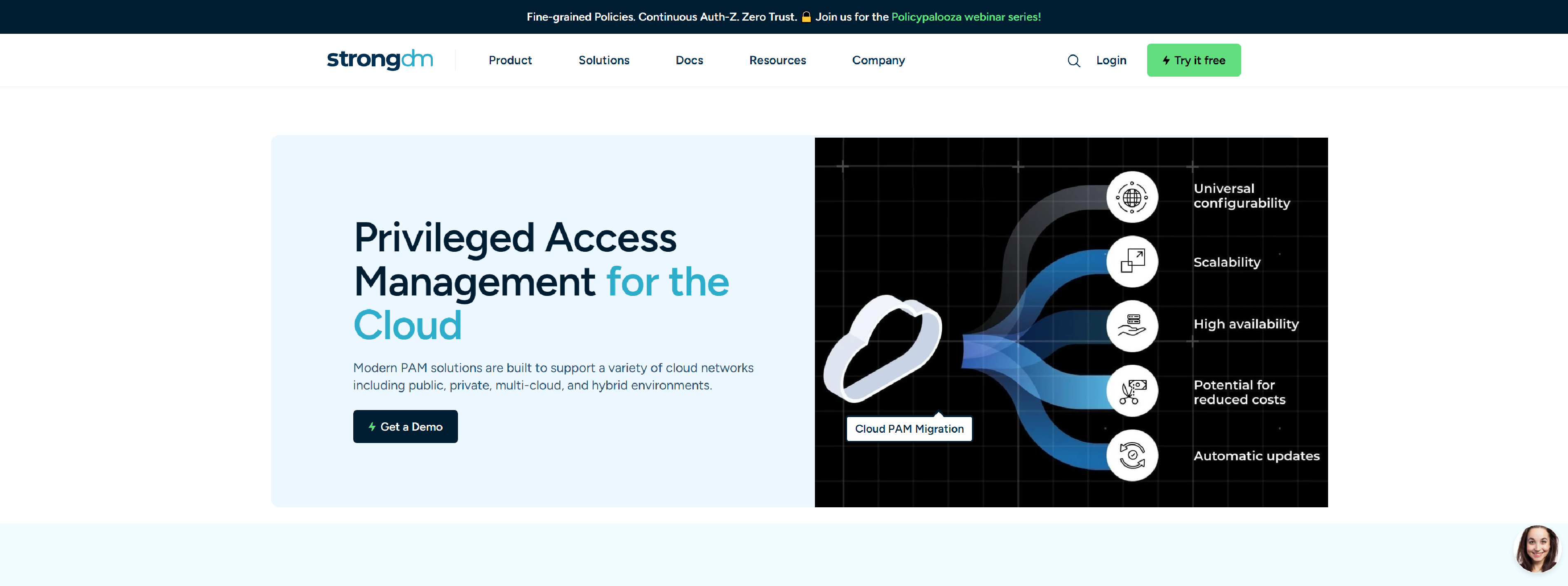
Strongdm – cloud privilege access management protects your organization with secure access to cloud applications and infrastructure so you can confidently adopt new technologies that save money and drive revenue to the business.
- PAM made for the cloud
- Innovate, don’t stagnate
- Cloud-Native Access Management
Bravurasecurity
Bravura Privilege cloud architected PAM & PSM solution secures access to elevated privileges including administrator accounts & security groups.
- Discovers and classifies privileged accounts and security groups
- Randomizes passwords and stores them in an encrypted, replicated vault
- Requires strong authentication before granting access
- Enforces pre-authorized and one-time access policy, to grant temporary access to privileged accounts, security groups, and even temporary SSH trusts
- Launches interactive privileged sessions using native and web-based RDP/SSH clients, locally installed software clients, and secure browser sessions for web applications
- Eliminates static embedded and service account passwords
- Logs access requests and sessions, including video capture and key-logging
Delinea
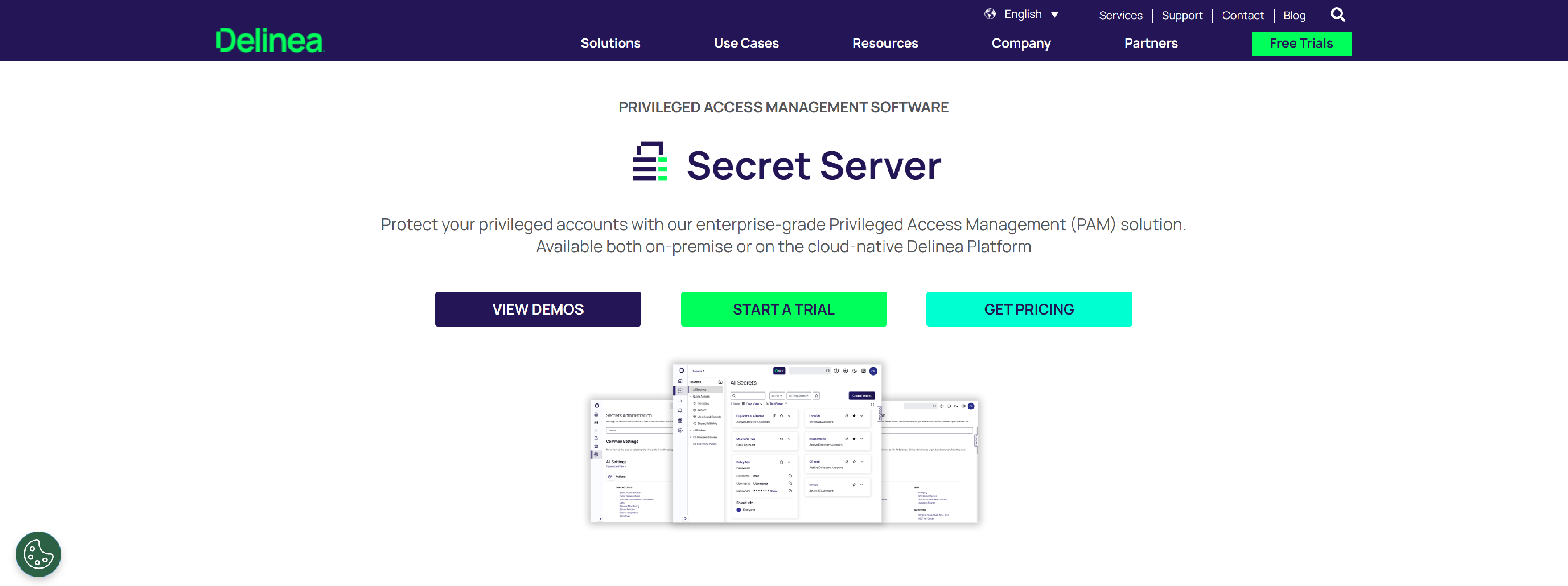
Delinea’s intelligent PAM, authorization, and identity security solutions to secure privileged access across your organization in real time.
- Secure Vault and Password Manager
- Access Control
- Automation
- Session Monitoring & Control
- Advanced Scripting
- Service Account Governance
- Distributed Engine (Scaling Out)
- Enhanced Auditing, Reporting and Compliance
- Approval Workflow
- Advanced Unix Features
- HA/DR
- Integrations Marketplace in Delinea Platform
Selection Criteria For the Best Cloud Privileged Access Management Solutions
When selecting the best Cloud Privileged Access Management (PAM) solution, it’s important to focus on specific criteria that address the unique needs of cloud environments. Here’s a detailed guide to help you evaluate potential solutions:
1. Cloud-Specific Security Features
- Cloud Integration: Ensure the PAM solution integrates seamlessly with various cloud platforms (e.g., AWS, Azure, Google Cloud) and services.
- Granular Access Control: Ability to define and enforce access policies based on cloud resources, roles, and contexts.
- Session Management: Monitor and record privileged sessions in cloud environments to detect and respond to suspicious activities.
2. Scalability and Flexibility
- Elastic Scalability: Ability to scale with the dynamic nature of cloud environments, accommodating varying workloads and user counts.
- Flexible Deployment: Options for both SaaS (Software as a Service) and hybrid deployments to fit different organizational needs.
3. Integration Capabilities
- API and Automation: Support for APIs and automation tools to integrate with existing cloud services, DevOps pipelines, and IT operations.
- Third-Party Integrations: Compatibility with other security solutions and management tools (e.g., SIEM, IAM systems).
4. User Experience and Management
- Ease of Use: An intuitive user interface for administrators and end-users to streamline management tasks.
- Administrative Efficiency: Features that simplify administration, such as automated workflows, role-based access management, and centralized policy enforcement.
5. Compliance and Reporting
- Compliance Support: Features that help meet regulatory requirements specific to cloud environments (e.g., GDPR, CCPA, HIPAA).
- Advanced Reporting: Detailed logging, audit trails, and customizable reporting to track and analyze privileged access and activities.
6. Risk Management and Threat Detection
- Anomaly Detection: Capabilities to detect unusual behavior or potential threats in real-time using behavioral analytics and threat intelligence.
- Incident Response: Tools and processes for responding to and mitigating incidents involving privileged access.
7. Cost and Licensing
- Transparent Pricing: Clear and predictable pricing models that reflect the scale and features needed for your organization.
- Value for Money: Assessment of the cost relative to the features and benefits provided by the solution.
8. Vendor Support and Reputation
- Vendor Track Record: Evaluate the vendor’s reputation, market presence, and customer reviews in the PAM space.
- Support Services: Availability of reliable customer support, training resources, and professional services for implementation and ongoing support.
9. Customization and Policy Management
- Customizable Policies: Ability to create and enforce custom access policies tailored to your organization’s specific needs and security posture.
- Policy Management: Tools to manage and update access policies efficiently as organizational requirements evolve.
10. Implementation and Transition
- Ease of Implementation: Assessment of how easily the solution can be deployed and integrated into your existing cloud environment.
- Migration Support: Assistance with migrating from existing PAM solutions or manual processes to the new system.
By focusing on these criteria, you can ensure that the Cloud PAM solution you choose will effectively protect your cloud resources, comply with regulations, and fit your organizational needs and budget.
Three key takeaways from this buyer’s guide to assist in your decision-making process
1. Prioritize Security and Compliance Features
Key Considerations: Ensure the PAM solution provides robust security features such as granular access control, session monitoring and recording, password management, and multi-factor authentication. Additionally, check for compliance support with relevant regulations and standards to ensure your organization meets its legal and industry obligations.
2. Evaluate Integration and Scalability
Key Considerations: Assess how well the PAM solution integrates with your existing IT infrastructure, including cloud platforms and other security tools. Also, consider its scalability to accommodate growth in users, systems, and data, ensuring that it can adapt to your organization’s evolving needs.
3. Consider Cost, User Experience, and Vendor Support
Key Considerations: Look for a solution that offers a good balance of cost-effectiveness and value. Evaluate the user experience, including the ease of use and administrative efficiency. Additionally, research the vendor’s reputation and the quality of their support services to ensure you receive adequate assistance and resources.
These takeaways can guide you in selecting a PAM solution that aligns with your organization’s security needs, operational requirements, and budgetary constraints.
How much do Cloud Privileged Access Management tools typically cost?
The cost of cloud Privileged Access Management (PAM) tools can vary significantly based on several factors, including the vendor, the features and capabilities of the solution, the scale of deployment, and the pricing model. Here’s a general overview of the factors influencing cost and typical pricing ranges:
Pricing Models
- Subscription-Based: Most cloud PAM solutions use a subscription-based pricing model, where you pay a recurring fee (monthly or annually) based on factors such as the number of users, endpoints, or features.
- Per User or Per Endpoint: Some solutions charge based on the number of users or endpoints being managed.
- Tiered Pricing: Vendors may offer tiered pricing based on different feature sets or levels of service.
Typical Cost Ranges
- Small to Mid-Sized Organizations: For smaller organizations or limited deployments, costs can range from $5,000 to $30,000 per year. This often includes basic features and a limited number of users or endpoints.
- Medium to Large Organizations: For larger deployments with more advanced features and a greater number of users or endpoints, costs can range from $30,000 to $100,000 per year or more.
- Enterprise Solutions: For large enterprises requiring extensive customization, advanced features, and high scalability, costs can exceed $100,000 annually. Some enterprise solutions are priced on a case-by-case basis, depending on specific requirements.
People Also Ask
Q1: What is Cloud Privileged Access Management (PAM) software?
A1: Cloud Privileged Access Management (PAM) software is a security solution designed to manage and secure access to critical cloud resources and systems by users with elevated privileges. It helps control, monitor, and audit privileged access to prevent unauthorized use and reduce security risks.
Q2: Why is Cloud PAM important?
A2: Cloud PAM is important because it addresses the risks associated with privileged access in cloud environments, such as unauthorized access, data breaches, and insider threats. By managing and monitoring privileged accounts, PAM ensures that only authorized users have access to critical systems and data, thereby enhancing overall security and compliance.
Q3: How does Cloud PAM differ from traditional PAM solutions?
A3: Cloud PAM differs from traditional PAM primarily in its focus on cloud environments. While traditional PAM solutions are often designed for on-premises systems, Cloud PAM is tailored to address the unique challenges of cloud infrastructure, such as dynamic resource allocation, multi-cloud environments, and cloud-native security needs.